Europe took a big step towards Digital Operational Resilience last week by issuing half of its new final technical standards one year from its implementation deadline.
JWG has analysed the new, final standards and the second batch of DORA consultations with other technology efforts underway across the globe.
We find that while some welcome clarity on Europe’s approach has emerged, there are many areas of divergence in the detailed approach to de-risk global technology infrastructure.
Collaboration will be key getting these standards right. That’s why we strongly urge everyone to tune in to RegCast and attend our annual RegTech conference on 7 February in London!
Context
With less than a year to go firms and their suppliers are racing to get ready for new DORA standards which landed last week as promised.
The three European agencies EBA, EIOPA and ESMA have taken on board industry feedback and produced new standards which firms now have 1 year to prepare.
As we wrote last summer, with tough new risk controls and thousands of suppliers in your technology supply chain implementation programmes are struggling to keep pace.
The second batch of EU consultations is now open until March with a hearing on 23 Jan. By July, the full set of standards is due leaving roughly 6 months for firms to get everything into place.
However, UK, US, and international standard setters are also setting standards for operational resilience which will take effect in a similar timeframe.
The policy efforts are not all aligned and, as highlighted by a November ‘Managing Cloud Risk’ paper by the Bank of International Settlements which suggest game-changing regulatory intervention like direct supervision of Cloud Service Providers (CSPs) is requried.
Calls for clarity – answered?
The first batch of DORA consultations elicited comprehensive responses from industry stakeholders. Organisations such as FIA, FESE, and EFAMA provided detailed feedback on various aspects:
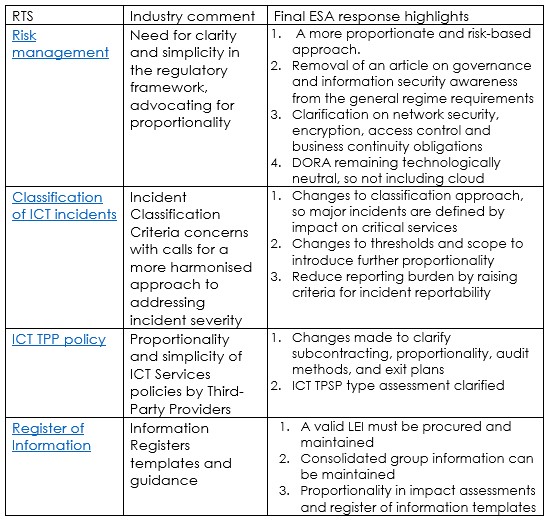
AFME were quick to respond to this showing concern over the ambitious 12-month timeframe for implementing these rules for DORA. They highlighted challenges in setting up manual risk management practices from scratch and emphasised the need for a proportionate and phased enforcement approach, particularly regarding supplier contracts.
DORA Batch 2 Consultations
The second batch of consultations introduces components critical for DORA were published on the 8th December 2023 and feedback is due by the 4th March.
Incident reporting
RTS and ITS on Content, Timelines, and Templates on ICT-Related Incident Reporting (Article 20) focuses on reporting details for major incidents.
Proposed harmonised timelines for financial entities within DORA are set out:
- Initial report within 4 hours of classification, no later than 24 hours from detection.
- Intermediate report within 72 hours or upon recovery to normal business.
- Final report within 1 month from classification.
- The content of major incident reports aims to strike a balance between essential information for competent authorities and minimal reporting burdens on financial entities. Additionally, the draft RTS introduces a concise content structure for notifications on significant cyber threats.
Incident cost and losses
Guidelines on Aggregated Costs and Losses from Major ICT-Related Incidents (Article 11(1)) specify the method to estimate annual costs and losses caused by major ICT-related incidents.
Aligned with technical standards for incident reporting, they introduce a reporting framework covering gross costs, financial recoveries, and net costs by major ICT-related incidents. The focus is on utilizing figures from validated financial statements within an accounting year.
Cyber
RTS on Threat-Led Penetration Testing (Art.26(11)) mandates advanced testing via Threat-Led Penetration Testing (TLPT) every 3 years for certain financial entities.
It specifies criteria for identifying entities requiring TLPT, requirements and standards for internal testers, and the entire lifecycle of TLPT, from testing methodology to results, closure, and remediation.
Subcontracting
RTS on Subcontracting of Critical or Important Functions (Art.30(5)) addresses subcontracting of ICT services supporting critical functions. Specifications for risk assessment, contractual arrangements, monitoring, information on material changes, and exit and termination rights concerning subcontracted services are provided.
Vendor oversight
Guidelines on Oversight Cooperation between the ESAs and Competent Authorities (Article 32(7)) cover cooperation and information exchange between the ESAs and competent authorities. These guidelines encompass general considerations, designation of critical ICT third-party service providers, oversight activities, and follow-up of recommendations.
RTS on Oversight Harmonisation (Art.41(1)) aims to harmonise requirements across regulations, ensuring efficient oversight conditions for critical third-party service providers. It specifies information to be provided in the application for voluntary designation as critical, the content and format of information submitted to the Lead Overseer, and details of competent authorities’ assessment based on recommendations of the Lead Overseer.
The proposed timelines for incident reporting impose stringent requirements on financial entities, while guidelines on aggregated costs emphasise a reporting framework aligned with financial statements.
Mandated Threat-Led Penetration Testing every 3 years poses rigorous testing criteria for specific financial entities. The RTS on Subcontracting outlines detailed specifications for critical ICT services. Guidelines on oversight cooperation and RTS on oversight harmonisation stress efficient collaboration for critical third-party service providers.
Overall, these developments amplify reporting obligations, testing requirements, and comprehensive frameworks for subcontracting and oversight in the financial sector.
Draft Regulations from the European Commission
The European Commission has taken significant steps in supplementing DORA through draft regulations which specify the criteria for the designation of ICT third-party service providers as critical. They have also taken pains to establish a method for determining oversight fees to be charged by the Lead Overseer and the way in which those fees are to be paid.
Designation of Critical ICT Third-Party Service Providers draft regulation outlines a two-step assessment process, considering quantitative and qualitative sub-criteria to designate ICT third-party service providers as critical. Factors such as operational impact on financial stability, interconnectedness, and critical functions supported by ICT services are considered.
Oversight fee regulation focuses on charges by the Lead Overseer to critical ICT third-party service providers. It introduces a calculation methodology for annual supervisory fees, emphasising full cost recovery and proportionality to the turnover generated by ICT service providers.
The proposed two-step assessment process for designating Critical ICT Third-Party Service Providers introduces comprehensive criteria, including operational impact and interconnectedness, influencing the landscape of critical service providers. Additionally, the introduction of oversight fees determined by the Lead Overseer emphasises a calculated methodology for annual supervisory fees. This move underscores a commitment to full cost recovery and proportionality relative to the turnover generated by ICT service providers. Overall, these draft regulations aim to enhance the robustness of oversight mechanisms and ensure a fair and proportionate financial burden on critical ICT third-party service providers.
Global Comparison
UK, US and the Financial Stability Board (FSB) standard setters have also been contributing to the standards debate and implementers will need to reconcile gaps in the register of information, guidelines of losses from incidents and align to a common global framework.
The latest standards to come out for each are the UK’s consultation CP26/23 on proposed rules and expectations for critical third parties, the US’s proposed operational resilience framework for futures commission merchants, swap dealers, and major swap participants, and internationally the FSB’s toolkit for enhancing third-party risk management and oversight.
Comparing the UK, the US, and international standards to DORA shows where the divergence lies:
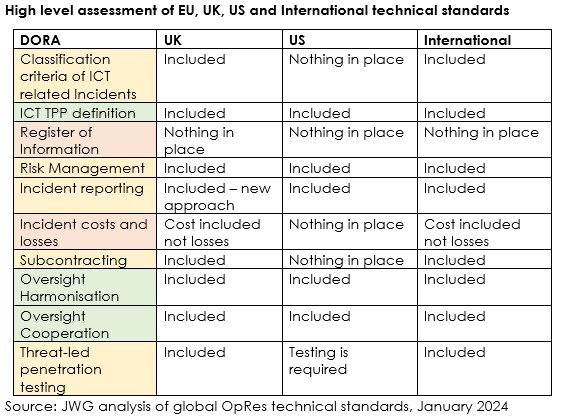
Europe is alone in requiring information to be reported and having full guidelines on costs and losses from ICT incidents, while the US need to develop more rules for the classification of ICT incidents, guidelines on potential costs and losses from ICT incidents, and subcontracting assessments to keep pace with other regulators.
The proposed US rule requires swap dealers and FCMs to align their operational resilience programs with generally accepted standards and industry best practices, such as NIST or ISO. They look more towards annual assessments, testing, and updates to reflect a commitment to adaptability in the face of evolving threats.
The Bank of England and FCA’s joint operational resilience guidelines for critical third parties prioritise a risk-based approach. The guidelines ensure thorough consideration of disruptions, emphasising the criticality of maintaining services and protecting the stability of the financial sector.
The FSBs toolkit for financial institutions and authorities provides a comprehensive global framework for enhancing third-party risk management and oversight. The toolkit focuses on collaboration and addresses challenges associated with third-party dependencies on a global scale.
Overall, while the US and the UK share a commitment to aligning operational resilience with industry best practices, the UK places greater emphasis on a risk-based approach. Internationally, the FSB’s toolkit serves as a collaborative global framework, recognising the need for unified approaches to third-party risk management.
Managing cloud risk
The ESA’s decision to keep DORA technology neutral, which was stated in the ESA’s first set of final draft technical standards under DORA, and with none of the international work so far including cloud technology, the BIS has published a view on cloud that should also be on the 2024 radar.
The widespread adoption of cloud technology has brought about remarkable efficiency gains but has also presented new challenges, particularly for financial institutions that heavily depend on cloud service providers. The BIS report on managing cloud risk and some considerations for the oversight of critical cloud service providers in the financial sector gives some essential insights.
Financial institutions are urged to scrutinise and actively manage their dependencies on cloud services. This involves a comprehensive evaluation of the critical functions supported by these services and their potential impact on overall operational resilience.
Addressing potential vulnerabilities is paramount in the oversight of critical cloud service providers. Financial entities must proactively engage in risk mitigation strategies, ensuring that potential points of failure within the cloud infrastructure are identified and remediated.
The BIS report highlights the necessity for robust oversight mechanisms to mitigate operational risks associated with cloud service providers. This includes implementing effective governance structures, continuous monitoring, and clear communication channels to address emerging challenges promptly.
As financial institutions globally grapple with the intricate task of managing critical cloud risks, a proactive and comprehensive approach to oversight becomes imperative. The nature of cloud technology necessitates a forward-thinking approach, ensuring the continued resilience and security of financial systems in an ever-evolving digital landscape.
Conclusion
As JWG research showed in 2022, new regulation will fundamentally change the landscape for the biggest technology providers.
The recent release of some final DORA standards, one year before the implementation deadline, has given us an insight into Europe’s approach towards Digital Operational Resilience. However, with many other resilience standards being developed worldwide, there are clear areas of divergence that cannot be ignored.
Collaboration will be key in navigating this complex transition towards global technology safety. This is why we strongly urge everyone to not miss out on the opportunity to get involved and stay updated through JWG’s RegCast series and our annual RegTech conference on 7 February.
Digital risks 2024: AI, Cyber, OpRes, OpRisk, TPRM